Get Rid of Circumventing System Policy
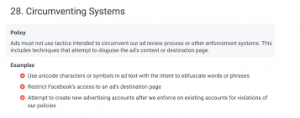
Circumventing System Policy is a flag that shows up on your ad account when advertising platforms like Google Ads and Facebook identify a violation of their ad guidelines. These guidelines are established to prevent advertisers from attempting to bypass or exploit their ad review systems or advertising systems. This is done to maintain a safe and trustworthy advertising ecosystem for both users and businesses. Circumventing System Policy violations may lead to disapprovals, suspensions, and even permanent bans on advertising accounts.
Some examples of this are cloaking, deceiving your audience in your ad content, misrepresenting your business or website, etc. If you are receiving this message on your ad account, it is important to understand the root cause and take steps to rectify the issue. If you are not sure how to do this, it is best to seek professional help from a certified digital marketing agency or Google Ads expert company.
It is also important to stay informed about these changes as these platforms may change their policies on a regular basis. By staying updated on these changes and adhering to them, you can minimize your chances of getting a suspended account in the future. This is the best way to avoid having your ad campaigns impacted by these issues and continue to drive valuable traffic to your business.
How Do I Get Rid of Circumventing System Policy?
Getting rid of circumventing systems policy requires a multi-faceted approach that involves both preventive measures and proactive enforcement strategies. Circumventing systems policies can pose significant risks to the security and integrity of an organization’s network, data, and operations. Here’s how you can address this challenge effectively:
Start by educating employees about the importance of systems policies and the risks associated with circumventing them. Make sure they understand the potential consequences for both themselves and the organization. Develop clear and comprehensive systems policies that outline what is and isn’t allowed within the organization. Clearly communicate these policies to all employees and ensure they understand their responsibilities.
Implement technology solutions such as firewalls, access controls, and monitoring tools to detect and prevent circumvention attempts. Regularly update and patch these systems to address emerging threats. Enforce strict user access management policies to ensure that employees only have access to the systems and data necessary for their roles. Regularly review and update user permissions to minimize the risk of unauthorized access.
Implement robust monitoring systems to track user activity and detect any attempts to circumvent systems policies. Encourage employees to report any suspicious behavior or policy violations they encounter. Clearly define the consequences for violating systems policies, and consistently enforce them. This could include disciplinary action, such as warnings, fines, or termination, depending on the severity of the violation.
Conduct regular audits and assessments of your systems and policies to identify any weaknesses or vulnerabilities that could be exploited for circumvention. Use the findings to continually improve your security measures. Foster a culture of compliance within the organization by recognizing and rewarding employees who adhere to systems policies. Encourage open communication and feedback to address any concerns or challenges they may face in following the policies.
By taking a proactive and comprehensive approach to addressing circumventing systems policies, organizations can better protect their assets and mitigate the risks associated with unauthorized access and misuse of technology resources.